 On October 21, a massive cyberattack made many popular websites (such as Twitter, Netflix and Amazon) inaccessible or slow. This cyberattack is notable both because of the large scale of the assault and because it used an emerging form of malware called “Mirai” which infected common devices, such as cameras, printers and baby monitors.
On October 21, a massive cyberattack made many popular websites (such as Twitter, Netflix and Amazon) inaccessible or slow. This cyberattack is notable both because of the large scale of the assault and because it used an emerging form of malware called “Mirai” which infected common devices, such as cameras, printers and baby monitors.
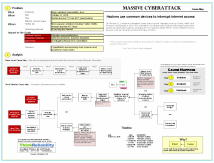
The cyberattack is currently being investigated and many details about it are not yet known, but an initial Cause Map can be built to help clarify and document the facts that are available. Cause Mapping is a format for performing a root cause analysis that visually lays out the cause-and-effect relationships that contributed to an issue. The most common reason for building a detailed Cause Map is to aid the investigation process by ensuring that all potential causes are considered and as a means to track all the known information and open questions. A high-level Cause Map can also be helpful when explaining a complex issue, such as a cyberattack, to the general public or management, who may not be familiar with the technical details.
The first step in the Cause Mapping process is to define the problem by filling in an outline with the basic background information for an issue, such as the time and date. How the issue impacted the overall organizational goals is also documented on the Outline. Once the problem is clearly defined, the next step is to analyze the problem by building the Cause Map. The Cause Map is built by asking “why” questions and adding cause boxes.
So why were websites inaccessible or slow? Domain Name System (DNS) provider servers were overwhelmed and DNS is needed for end users to access websites. (When there is more than one answer to a why question, the causes are both added to the Cause Map vertically and separated with an “and”. Continue asking “why” questions for each new branch of the Cause Map.) DNS functions as a switchboard for the internet and is essential infrastructure that needs to function for users to be connected to websites. The DNS servers were overwhelmed because there was a massive spike in traffic because they were targeted by a large-scale distributed denial of service attack.
In a denial of service attack, a website receives a large number of malicious requests that makes it difficult for the website to answer legitimate requests. In this case, tens of millions of IP addresses were used to generate the malicious requests because hackers had infected millions of common devices with “Mirai” malware and then used the devices to generate the malicious requests. Hackers were able to infect so many devices for several reasons. First, there simply are more internet-connected devices in homes each year. The internet of things continues to grow and now includes everything from refrigerators to baby monitors to home routers. The cybersecurity on these devices tends to be less robust than the security on computers or cell phones, meaning they are generally easier to gain access to and infect with malware. Whatever security is present on these devices is also not generally updated regularly the way a home computer typically is.
Multiple groups have claimed responsibility for the cyberattack, but officials are still working to determine the source of the attack and the motivation. Experts are also working on how to increase the security of necessary internet infrastructure to mitigate the impacts of future attacks. There will likely continue to be a learning curve as more and more devices are connected to the internet and we struggle to learn how to keep them safe and prevent them from being used for nefarious purposes.


![Document Your Root Cause Analysis Investigation Like a Pro [Download the Free Template]](https://hubspot-no-cache-na2-prod.s3.amazonaws.com/cta/default/2164270/8df3876c-a4ed-43bf-b6cc-e53f59a6f21a.png)